In the last entry I wrote a little about block ciphers, now in this entry I'm going to wrote about the MacGuffin block cipher.
Origin
MacGuffin is one of the earsliest a block cipher design created in December 1994 by Bruce Schneier and Matt Blaze at a Fast Software Encryption workshop. The name of this cipher comes from the acronym of the class of ciphers to which it belongs, that is the Generalized Unbalanced Feistel Networks, GUFN's, hence MacGuffin.
Purpose of MacGuffin Cipher
It was intended as a catalyst for analysis of a new cipher structure, known as Generalized Unbalanced Feistel Networks (GUFNs). This unbalanced Feistel network has 32 rounds and it is similar in structure to the NSA's Skipjack algorithm.
Another purpose of this algorithm was to explore the security properties of unbalanced Feistel networks.
Description
MacGuffin is also similar to Data Encryption Standard (DES), it takes a block of 64 bits of plain text to encrypt, takes a secret key that is 128 bits long, performs its transformation based on the key, and produces as output 64 bits of text that should be incomprehensible to anyone who doesn't know the secret key.
Their main change compared with DES, is that MacGuffin was spliting the DES 64 bits data block into two unequal halves in the Feistel network, 48 bits of the 64-bit data block are fed through the round function, whose output is XORed with the other 16 bits of the data block.
In other words this algorithm split the text into two parts with one part repeatdly modified according to a keyed function of the other part. In each round of the cipher it modifies only 16 bits according to a function of the other 48 bits.
Schneier and Blaze recommended using 32 rounds, and specified MacGuffin with a 128-bit key.
We were talking abour Feistel cipher and Feistel network, but what is that?
Well a Feistel cipher is a symmetric structure used in the construction of block ciphers. A Feistel network is an iterated cipher with an internal function called a round function
Principles
Each round operates only with 16 bits and we use 32 rounds. Because there are twice as many rounds, however, there are also a total of twice as many key bits XORed with the control blocks.We adapt our S-boxes directly from those of DES. The eight DES S-boxes each produce four bits of output. Since we require only two bits from each (that give us a total of 16 bits), we use only the "outer" two output bits from each S-box.
In each round, each control block bit is XORed with one derived key bit and provides one input to exactly one S-box. The control bits are mapped 1 : 1 to S-box inputs according to a fixed permutation. This permutation was designed so that each S-box receives two of its six inputs from each of the three registers in the control block.
Algorithm
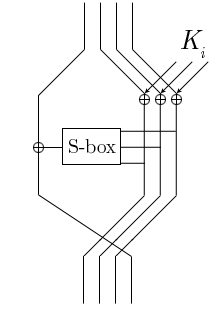
EncryptionThis diagram in the right side shows one round of MacGuffin block cipher.
- The 64-bit data block is divided in four 16-bit words (each word is represented in the diagram by one line).
- The rightmost three words are XORed with subkey bits derived from the secret key.
- They are then fed through eight S-boxes, each of which takes six bits of input and produces two bits of output.
- The output (a total of 16 bits) is then recombined and XORed with the leftmost word of the data block.
- The new leftmost block is then rotated into the rightmost position of the resulting data block.
- The algorithm then continues with more rounds until the 32 round.
Decryption
MacGuffin's key schedule is a modified version of the encryption algorithm itself.
To decrypt am encrypted message is very easy because MacGuffin is a Feistel network; simply run the encryption algorithm in reverse.
Vulnerabilities
Vincent Rijmen (of AES/Rijndael fame) and Bart Preneel performed a cryptanalysis of MacGuffin and showed that it was quite vulnerable to differential cryptanalysis and linear cryptanalysis, but also showed it could be significantly strengthened by making only a few minor changes in its use of S-boxes. This happened during the same workshop MacGuffin was presented.The algorithm was experimental, intended to explore the security properties of unbalanced Feistel networks. The cryptanalysis proceeded very quickly, so quickly that the cipher was broken using differential cryptanalysis at the same workshop by Vincent Rijmen and Bart Preneel. They also tried attacking MacGuffin with different S-boxes, taken directly from DES. This version was slightly stronger.
Example
Here are some pseudocodes about the key setup, encryption and decryption of this block cipher, I found it in this pdf of Bruce Schneier paper-macguffin.pdf
Encryption
Decryption
Keys Setup
Sources



Hay detalles con la ortografía y faltó un ejemplo pequeño a mano. Van 6 pts.
ReplyDelete